The Existential Risk of Q-Day
As we move into the growing quantum age, the rapid rise of quantum computing is beginning to create new challenges and risks for India’s growing digital sector. Modern cryptographic mechanisms specifically RSA and Elliptic Curve Cryptography (ECC) ensure the confidentiality and trust of the globally, yet they face an existential threat from the rise of Cryptographically Relevant Quantum Computers (CRQCs). Shor’s algorithm has already demonstrated the theoretical vulnerability of current RSA Encryption which is widely used. With experts suggesting that “Q-Day” may arrive as early as 2029.
The Department of Science and Technology (DST), Govt of India has established a Task Force under the National Quantum Mission (NQM) to secure the nation’s digital infrastructure against “Harvest Now, Decrypt Later” (HNDL) threats. This transition is not a routine upgrade; it represents a fundamental shift in digital trust, moving from research pilots toward structured national deployment. We will analyse the report of the task force on Implementation of Quantum Safe Ecosystem in India.
Key aspects of the roadmap are as follows:
India’s Dual-Track Strategy
India’s roadmap opts the strategic “Middle Path” that rejects the singular approach focus often seen in Western countries. India’s approach balances the utility of global standards with the security of indigenous hardware. This approach rejects the “singular” focus often seen western countries specifically the US and UK, which prioritizes algorithmic upgrades i.e. Post Quantum Cryptography (PQC) while largely dismissing hardware-based Quantum Key Distribution (QKD) owing to the cost factor.
Hybrid Tracks: PQC and QKD
The framework integrates two distinct pillars to create a robust security backbone:
- Post-Quantum Cryptography (PQC): This approach utilizes software-based algorithmic updates to protect existing digital infrastructure, while cost effective this approach is not full proof, the roadmap deploys PQC for broad enterprise and last-mile connectivity where scalability is key, this way the sectors which need development are not restrained.
- Quantum Key Distribution (QKD): Provides information-theoretic security based on the physical properties of light, creating a hardware-based strategic backbone through inter-city fiber optics and satellite-enabled links, the roadmap simultaneously funds a National Quantum-Safe Network (NQSN) using QKD backbones for strategic inter-city links, defence, and high-security sectors, where security is core factor and cannot play second fiddle.
Technological Sovereignty and the 4-Tier Framework A core theme of the National Quantum Mission is the pursuit of technology sovereignty, aimed to reduce the reliance on foreign equipment and to bolster Indigenous development. To achieve this, India has developed a four-tier assurance framework, as under:
- Level 1 (L1) : Basic conformance for low-risk consumer environments.
- Level 2 (L2A-C) : Secure assurance for medium-risk sensitive data.
- Level 3 (L3) : Enterprise-grade security for the banking and telecom sectors.
- Level 4 (L4) : Sovereign-grade security for critical infrastructure, mandating indigenous cryptographic implementations.
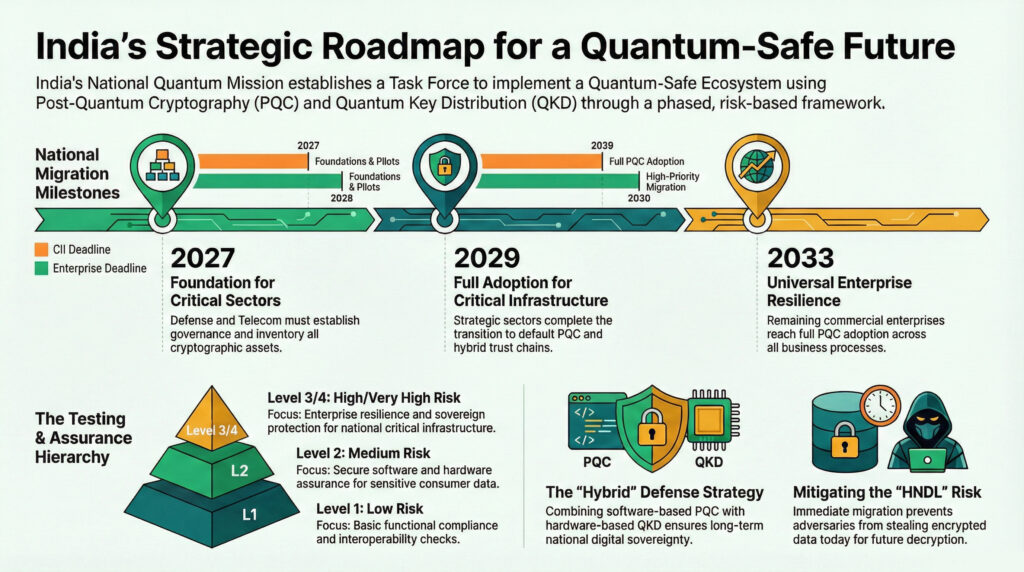
Fig 0.1 Machine Generated | Sourced from The Report
Implementation Roadmaps: Personas and Accelerated Timelines
To manage the uneven urgency of this migration, the Task Force categorizes organizations into specific “Personas”.
Urgent vs. Regular Adopters, the roadmap classifies its Critical Information Infrastructure (CII) including defence, power, and telecom as Urgent Adopters. These sectors are bound by a legal mandate to achieve full PQC adoption by December 31, 2029. In contrast, regular enterprises follow a baseline timeline extending to 2033.
A milestone-based transition
The migration is structured into three critical phases:
- Building Foundations (2027–2028): Identifying and taking inventory of cryptographic assets and initiating leadership pilots.
- Migrating High-Priority Systems (2028–2030): Enforcing a “no new classical-only” policy and upgrading Public Key Infrastructure (PKI).
- Full PQC Adoption (2029–2033): Transitioning to PQC-only trust chains and ensuring all digital signatures are quantum-safe.
Global Comparative Analysis: India and the P5 Nations
India’s roadmap positions it as a proactive global leader, with timelines significantly more aggressive than several P5 members.
| Feature | India | United States | China | United Kingdom |
| Primary Strategy | Dual track (PQC + QKD) | PQC-Centric | QKD-Heavy | Phased Roadmap |
| Critical Infra Target | 2029 | 2035 | 2027 (QKD Service) | 2031 |
| Standardization | Sovereign (L1–L4) | NIST Global Leader | Indigenous (ICCS) | NCSC/NIST Aligned |
While the NIST Bloc (USA and UK) remains skeptical of QKD for enterprise use, India aligns with the “Hybrid Approach” favoured by the EU and South Korea, refereed in their joint Digital Partnership going as far back as 2022 and its further development via various partnerships. Notably, India’s target for critical infrastructure is six years faster than the US federal target of 2035. Like China, India emphasizes sovereign standards; however, while India utilizes global algorithms like Kyber and Dilithium within its sovereign L4 framework, China has bypassed NIST entirely to develop indigenous algorithms.
Strategic Implications and Operational Challenges
The transition necessitates a fundamental shift in procurement and system architecture, governed by the principle of “Crypto Agility” i.e. ability to rapidly switch algorithms without system disruption.
Mandatory Procurement Shifts Starting in FY 2026–27, vendors would be mandated to submit a Cryptographic Bill of Materials (CBOM) to the Indian government. This structured inventory ensures transparency and enables rapid responses to future vulnerabilities.
Technical and Governance Barriers
The Task Force acknowledges several hurdles to successful migration:
- Legacy Complexity: Inflexible infrastructure often lacks the compute headroom for PQC overhead.
- Validation Gaps: Indigenous algorithms lack mature test vectors, and foreign OEMs are often reluctant to share necessary documentation for hardware validation.
- Interoperability: The coexistence of classical and quantum-safe algorithms increases the risk of “downgrade attacks”.
Conclusion: The Path Forward
India is treating the Cryptographically Relevant Quantum Computer “CRQC” threat as an imminent national security priority. By setting accelerated legal mandates and developing a indigenous/sovereign testing ecosystem, free from external control. The current approach seeks to immunize its digital economy against future decryption threats while fostering indigenous technological growth. However, the success of this roadmap depends on bridging current gaps in domestic testing capabilities and ensuring that the move toward PQC does not compromise the performance of legacy systems. The transition is expected to incur significant costs proportional to the US estimate of $7.1 billion highlighting the necessity for sustained executive oversight and dedicated funding, and overall coordination, since the roadmap hinges on all effected parties, working towards a unified goal, without holding back one another. While this brief outlook into the Quantum Roadmap is timely as to how it’s implemented and carried out remains to be seen, but on thing is for certain, India’s current deadline puts us far ahead of our competitors, refer the graph below for an overview.
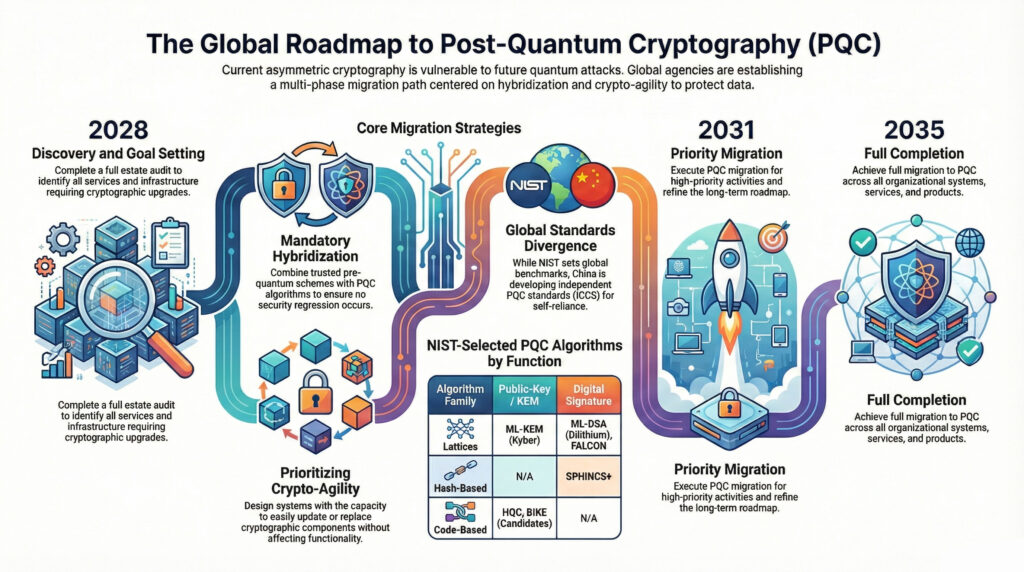
Fig 0.2 Machine Generated | Sourced from Publicly available Information
All readers of this article are encouraged to check the full roadmap for better clarity, since this article is summary of key elements.
https://dst.gov.in/sites/default/files/Report_TaskForce_PQMigration_4Feb26%20%28v1%29.pdf













