Introduction:
As the skies in Nagorno Karabakh were grim with Azeri UAVs (Unmanned Ariel Vehicle) targeting Armenian military targets such as tanks, artillery positions, and military installations. Seldom did the tank commander sitting inside an Armenian T-72A know that he would be the next target of the loitering armed UAV above him; which was sharing its visuals back to base later to be exploited for propaganda. Even as the governments of both countries engaged themselves in social media battles, proclaiming victory for the day and withholding their losses under the garb of plausible deniability. Keeping track of Armenia and Azerbaijan’s losses in the recent clashes in Nagorno-Karabakh were many OSINT analysts. Hidden behind millions of webpages and social media accounts, OSINT (Open Source Intelligence) handles collated several pieces of information and echoed the information to a broader audience for both private and public. All while the individual is possibly sitting behind a desk hundreds of miles away from the incident.
According to the document issued by the US Director of National Intelligence, OSINT is defined as “intelligence produced from publicly available information that is collected, exploited, and disseminated in a timely manner to an appropriate audience for the purpose of addressing a specific intelligence requirement”[1]. Opensource intelligence has risen into an effective form of information gathering and processing, compared to the traditional information collection model conducted by the print or visual media. Often diving into the world wide web, culling out information regarding a specific event or situation — the OSINT has grown into an essential community of information gatherers. While this article does not vouch for the authenticity of any such OSINT reports, its broad audience and impact in the general news stream certainly makes the OSINT community highly relevant to the modern audience.
The Overlapping fronts and the Catch 22s
OSINT traces its roots back in world war II through its creation as the US establishment of FBMS (Foreign Broadcast Monitoring Service) in 1941; it was responsible for monitoring and collating data from open sources such as foreign media & propaganda to use against the axis powers and during the Cold War[2]. After several stages of evolution throughout history, the organisation was renamed as the Open Source Enterprise (OSE) by the US government in 2015[3]. The start of the user-generated content in this decade has led to the boom of open-source information. The extensive usage of social media and other internet tools by billions of people has made personal information widely available and considerably less protected. As the OSINT realm now touches upon HUMINT (Human Intelligence); GEOINT (Geospatial Intelligence) with the availability of commercial satellite imagery which at times is right below the threshold of military satellite resolutions, and SIGINT (Signal Intelligence)— the scope of conventional information gathering has broadened and at times blurred.
The overlapping realms of OSINT.
Source: Williams, Heather J. and Ilana Blum, Defining Second Generation Open Source Intelligence (OSINT) for the Defense Enterprise. Santa Monica, CA: RAND Corporation, 2018. https://www.rand.org/pubs/research_reports/RR1964.html. Also available in print form.
Nowadays, Open Source Intelligence is extensively used in the corporate sector for analysing markets and future trends. However, concerns remain hitherto to the usage of corporate ‘gray data’ such as publically available patent details, business documents, technical reports, meeting minutes, and so forth. The use of such data can be detrimental to individual businesses and raises serious questions regarding the ethical usage of open-source information[4].
Thanks to social media, the OSINT handles have been striving to fill out the information vacuum in places of instability, violence, and political uncertainty in the public spheres. Often at times, acting on par with the conventional media reporting. Exploiting twitter as a popular platform to disseminate the information gathered by the OSINT handles, media houses have often quoted OSINT analysts like H I Sutton (@covertshores) for his extensive work on Naval equipment like Submarines and Ships through SATINT ( Sattelite Intelligence), and also Steffan Watkins, (@steffanwatkins) his analysis is often cited in relation with the Open Skies Treaty.
As the number of OSINT handles has been continuously increasing, the 2020 Cyber Threat Intelligence report states that 34% of OSINT practitioners that they had no prior experience with OSINT collection, and about 85% of them have little to no training in OSINT techniques and risks[5]. While the growing community of OSINT analysts is a welcome change, the following trend also leads to many open-ended questions regarding the OSINT community, such as the anonymity of the OSINT handles and accountability of their reports. As these handles experience a fast rise in their followers and the simultaneous ‘echo effect’ which is often associated with the fast spread of news in social media; the question of ethics followed in gathering the information and dissemination of such information to the audience remains to be answered, especially to curtail the spread of fake news which can cause severe damage to societies. Challenges also remain in regards to the concerns on privacy for the information collected from social media profiles[6].
The Indian Case study and Recommendations
In the summer of 2020, India’s northern borders with China were tense, with new standoffs in the Galwan valley and Pangong Tso in Ladakh. Interestingly, a new front was opening up in the realm of social media; as the information gap grew regarding the standoffs, the OSINT handles were key in putting out satellite imagery of the standoffs. The resolutions of the commercial satellite imagery offered by OSINT analysts were distinct enough to prove the rising tensions in respect to the increment in force levels and advancing positions. Prominent media handles quoted the OSINT analysis conducted by @detresfa of the recent standoffs with China, including in the Galwan Valley (Fig 2), while there was a diligent information gap by the two respective governments regarding the operational situation.
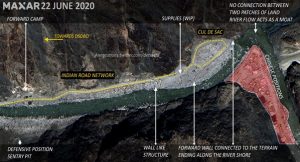
Fig 2: Sattelite imagery of the encampments in the Galwan Valley. Source: Twitter @detresfa_ https://twitter.com/detresfa_/status/1276039949154783233/photo/1
Recommendations:
- While the use of OSINT shall reduce the information gap during incidents, regulators need to check and ensure that there is no sensitive data published in open domains and ensure the sanctity of postures adopted by the forces in sensitive military situations is dissuaded from airing.
- Although OSINT is legal, the government must ensure a tight online protocol for its personnel to ensure Armed forces personnel and government employees’ identities or information put out by them are not utilised for malicious intent or ‘doxxed’[7].
- There is a need for certain regulations on information that can impact national security or cause serious damage to a community of people. Issues concerning individual data privacy should be addressed, and the existing laws towards ensuring the right to privacy must be strengthened.
- While OSINT tools can be a great way to research and investigate proactively, the same tools in the wrong hands could turn into a double-edged sword, primarily if used to promulgate terrorism, misinformation, and engage in cybercrimes. Therefore, there is a need for a proactive social media presence required by credible media outlets and the government to tackle misinformation spread by handles with malicious intent.
As conventional intelligence gathering by states through the means of espionage and theft of sensitive documents shall remain in the foreseeable future; meanwhile, open-source intelligence shall also merge between the two realms of intelligence collection. As the OSINT domain grows into a substantial size day by day with newer tools available to mine and process more data, OSINT technologies shall prove handy for states as well as to engage themselves in information warfare to achieve their interests. Finally, there is a need for an in-depth debate on the use of Open-source information to address the legal and ethical dilemmas surrounding the usage of data.
ENDNOTES
[1] Office of the Director of National Intelligence, U.S. National Intelligence: An Overview 2011, Washington, D.C., 2011, p. 54.
[2] Williams, Heather J. and Ilana Blum Defining Second Generation Open Source Intelligence (OSINT) for the Defense Enterprise. Santa Monica, CA: RAND Corporation, 2018. https://www.rand.org/pubs/research_reports/RR1964.html. Also available in print form.
[3] Aftergood, Steven. “Open Source Center (OSC) Becomes Open Source Enterprise (OSE).” Federation of American Scientists, October 28, 2015. https://fas.org/blogs/secrecy/2015/10/osc-ose/.
[4] Putman, Patrick. “What Is Open Source Intelligence?” United States Cyber Security Magazine, November 5, 2018. https://www.uscybersecurity.net/open-source-intelligence/.
[5] Rep. 2020 Cyber Threat Intelligence Report. The Cyber Security Insiders, 2020. https://www.cybersecurity-insiders.com/portfolio/2020-cyber-threat-intelligence-report/.
[6] Eijkman, Quirine & Weggemans, Daan. (2013). Open Source Intelligence and Privacy Dilemmas: Is it Time to Reassess State Accountability?. Security and Human Rights. DOI: 23. 10.1163/18750230-99900033.
[7] Doxxing is the practice of releasing collected data with malicious pertaining to individuals, businesses, government entities, etc. This is both illegal and unethical.















