Security is a cornerstone of development and progress in a free society. A basic and widespread understanding of the importance of security as a guarantee of citizens’ well-being and therefore the stability of the State itself is therefore essential. Added to the common risks and threats are new, typically transnational ones which are interconnected and increase their adverse impacts; and at the same time new flaws are emerging that facilitate their spread and impact. In this cyber age, cyberspace is the clearest example of a space that is accessible, loosely regulated and difficult to control.
Strategic assets:
‘Strategic assets’ is a relatively new term that arose in reference to the fast-forward development of economic globalisation in the 20th century and a new wave of an economic conflict or trade-war that has been leashed by the change in economic power centres. Therefore, the reorganisation of economic, political and strategic alliances connected with it. By strategic assets we mean generally any tangible or intangible asset or concern of substantial value in a given economy, state, or nation. Today, India is embroiled in a conflict with stateless/ proxy enemies who will resort to unprecedented tactics, both kinetic and non-kinetic, in sum hybrid warfare, to disrupt the stability in the country and eventually achieve their extreme goals. Strategic assets have national security implications because of their tactical value. [1]
When we look at the cyberattacks around the world, one of the first known cyber-attacks at a nuclear plant took place in 1992 when rogue programmer Oleg Savchuk deliberately infected the computer system of a plant in Lithuania with a virus. Savchuk was arrested and became a precautionary footnote in the history of nuclear security. In March 2007, engineers at the Idaho National Lab showed how 21 lines of computer code could cripple a huge generator. It was only through this jaw-dropping experiment, known as Aurora, that some energy industry officials came to accept that digital tools are capable of physical destruction. Two years later, the destructive potential shown in Aurora became a reality. The famed Stuxnet attack injected a formidable computer worm into Iran’s Natanz enrichment facility in 2009, destroying about 1,000 centrifuges. Another playground for hackers is the Ukrainian power grid, some of whom analysts have traced to Russia. In December 2015, a cyber-attack on Ukrainian grid which cut power for 225,000 people. [2]
Kudankulam nuclear power plant:
Recently, the Kudankulam nuclear power plant, located in India, was close to getting compromised. The power plant officials stated that Kudankulam and other Indian nuclear power plants “are stand-alone and not connected to outside cyber network and Internet. Any cyberattack on the Nuclear Power Plant Control System is not possible”. Well…this is kind-of-true. True, the cyber-attack can’t be accomplished electronically from the outside, but humans can physically get around that by portable devices. complacency is the biggest threat, which officials had until this attack.
Even Iran’s Natanz enrichment facility’s computers were “air-gapped”, still it was attacked, and attackers accomplished their mission. The attackers used portable media to deliver malware to “air-gapped” systems, or those with no direct or indirect connections to the internet. In doing so, the attackers refuted the notion that such a system was immune to hacking. An air gap is a concept of physically isolating critical computers or networks from insecure networks (such as the public Internet). In theory, devices on either side of this gap are unable to communicate, making an air gap an attractive option for securing the most important networks. In practice, security inspections often find unintended network connections to systems that are meant to be isolated. Evidence of malware infections on air-gapped computer systems is often discovered years after the initial infection. So, air gaps can be effective against unsophisticated and untargeted cyber threats — but not against targeted attacks from within. Worse, they often create a sense of complacency making it possible for a targeted attack perpetrated by a determined, well-resourced adversary to succeed.
Nuclear Threat Initiative (NTI) points out that targeted attacks go beyond network connections and generally leverage “witting or unwitting humans, or a long and difficult-to-defend supply chain, to deliver the attack.” These are pertinent to the Kudankulam attack. According to some agencies, it’s been speculated that the Kudankulam attack was by the North Korean DTRACK virus. The attackers managed the improbable feat of breaching and manipulating a nuclear facility’s heavily protected industrial controls. Kudankulam is the biggest nuclear power plant in India, with two 1,000 MW Russian VVER pressurized water reactors. In collaboration with Russia, the plant is adding four more reactors of the same size which will make Kudankulam Nuclear Power Plant one very large power source, producing over 47.4 billion kWhs per year. It should be protected better and efficiently. [3]
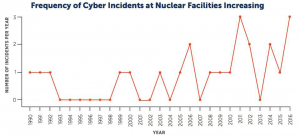
The figure above shows that the number of cyberattacks against nuclear facilities has significantly increased since 2000. [4]
The Fissile Materials Working Group’s more recent report also notes that organizations must transfer data into and out of their operational networks for a variety of reasons, and these are all pathways for attacks. New data have to enter even an air-gapped operational network to update its software and hardware. Most famously, the Stuxnet attack penetrated Iran’s air-gapped Natanz uranium enrichment facility in just this way. And the facility was well defended and isolated from the Internet. If an organization allows flash drives and USB keys to enter and exit their operational technology network, then data diodes, firewalls or switches have no capability to stop them. Organizations also allow external hardwares, e.g. laptops, mobile phones, etc. to enter and exit their operational technology network as part of facility and operations vendor maintenance. Commercial off-the-shelf software, that an organization does not really own, can be infected. [4]
To try to get ahead of the threat, NTI identified four overarching priorities, as well as specific actions, that if implemented would dramatically reduce the risk of damaging cyberattacks on nuclear facilities. They include: (A) Institutionalize cybersecurity, (B) Mount an active defence, (C) Reduce complexity, and (D) Pursue transformation.
CERT-In (Indian Computer Emergency Response Team) coordinates efforts on cybersecurity issues and is tasked with responding to cyberattacks, while the National Technical Research Organization is the elite technical intelligence agency. There are growing concerns that the country’s power infrastructure could be the next target of terrorists looking to cripple its economy. The issue has assumed greater importance as India now has an integrated national power grid.
An outlook for the future
Adversaries are getting smarter, they are growing in their ability to learn industrial processes and codify and scale that knowledge, and defenders must also adapt. It is essential to encourage the involvement of citizens and collaboration between
the public and private sectors and all the Public Authorities in their areas of responsibility because today’s risks and threats are not unconnected and cannot be addressed through isolated responses. Guaranteeing security is the responsibility of the Government, but it is also a task of everyone.
When it comes to being ready to avert such an attack, one needs to have the complete knowledge of the same, but it’s not possible, because successful attacks are rare, there is a small pool of data to learn from. Security experts say there is no substitute for putting an organisation’s cyber teams under the gun in an intense, credible scenario. It’s very important to understand the link between what’s happening in cyberspace and what’s happening in real life, if you don’t do that, it’s very easy to just think of these exercises as a game where you need to perform and get a good score and that’s it. The less that exercises seem like a game to participants, the better prepared they’ll be for the real thing. The challenge, however, is that exercises are technically rigorous, expensive, take many months to plan, and may require bringing in outside cyber expertise to drill plant personnel.
The alternate solution can be hiring third-party private cybersecurity agencies, like Britain’s larger nuclear operators, have recently begun hiring security firms to probe their computer networks for vulnerabilities. The present structure has failed to ensure that software on the plant had been updated or not and that employees were trained in security or not, to cope up with such incidents. Among nuclear executives, “accountability is going to drive better behaviour” on cybersecurity has seen the industry adapt its safety standards after the 1986 Chernobyl disaster, its security standards after the September 11 attacks, and its cybersecurity standards after Stuxnet. The guessing game of where the next attack might come from can be maddening. This changing digital landscape is prompting governments and energy companies to get more ambitious in how they drill for attacks. The goal is tighter communication and unalloyed trust between the government and operators of critical infrastructure. In the event of a serious cyberattack, nuclear operators would need to have agencies on speed dial to mitigate the damage. In the waning days of the Obama administration, US and British officials tested these lines of communication in an unprecedented exercise they called Ionic Shield. India needs to do the same to protect our strategic assets.
With an advancement in technology, cyber-attacks are becoming more subtle. Some hackers play the long game, lingering on peripheral networks for months in the hope of gaining a foothold into more critical systems. For network defenders, maintaining urgency in the absence of regular, successful attacks can be difficult. The shock value of events like Aurora and Stuxnet can only last so long as those who study them fall back into their routines. Rigorous exercises based on unnerving scenarios are critical to keeping engineers and cyber specialists on their toes.
‘‘The future is actuarial, history is forensic’’, now is the time to keep this phrase in mind and act promptly and efficiently to evade forthcoming attacks. It is essential that these priorities be implemented by coordinated actions among government, industry and regulators.
References:
[1] Sehgal, Ikram. (December 13, 2019). Keeping strategic assets secure. Retrieved from https://dailytimes.com
[2] Lyngaas, Sean. (Jan 23, 2018). Hacking Nuclear Systems Is The Ultimate Cyber Threat. Are We Prepared?. Retrieved from https://www.theverge.com
[3] Utpal Bhaskar, Utpal. (20 Nov 2019). India confirms malware attack at Kudankulam nuclear power plant. Retrieved from https://www.livemint.com
[4] Conca, James. (Nov 8, 2019). How Well Is The Nuclear Industry Protected From Cyber Threats?. Retrieved from https://www.forbes.com















