Abstract
At the end of March 2024, the IBM subsidiary Red Hat Inc gave an urgent notice of a malicious backdoor in the XZ utilis library, a popular data compression tool used across various Linux distros. The backdoor, which was said to have been introduced through a series of obfuscated malicious code committed to the Tukaani Project via the Tukani GitHub repository, can be termed a crucial vulnerability as it affects many Linux users. This commentary will analyse the said instance and further analyse its probable implications.
Keywords: XZ Utils, GitHub, Tukaani, Linux, Backdoor, Open-Source packages
Introduction
On 28th March 2024, a backdoor was identified in the XZ Utilis library, a data compression tool utilised by variant Linux distributions. The backdoor identified as CVE-2024-3094 (NIST, 2024) was located in the upstream tarballs of xz, starting with the version 5.6.0 and 5.6.1 libraries. For context, a tarball of XZ, or a .tar.xz file, is a compressed archive format that combines the tar utility with the XZ compression algorithm. This format is widely used in Linux and UNIX systems for compressing files and folders, sharing them over networks and storing them on disks. The .tar.xz extension indicates that the file is a tar archive that has been compressed using the XZ compression algorithm. The malicious code was found by Microsoft employee Andres Freund, who identified that the code was introduced to the Git library over a series of code commits to the Tukaani Project on GitHub. According to him, user Jia Tan, or JiaT75, added the malicious code over time. He explains that either the committer is directly involved or their system must be severely compromised while giving lesser credence to the latter. (Freund, 2024).
GitHub, owned by Microsoft, has since disabled the repository, and the library is currently updated and accessible.
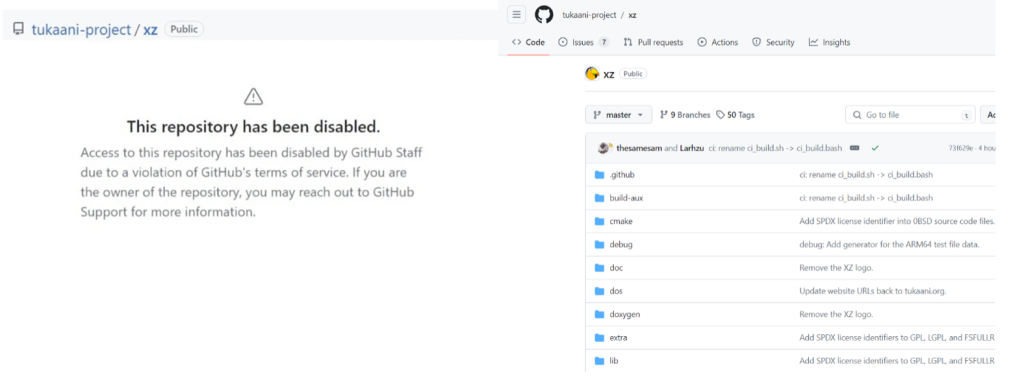
Figure 01 : Source (Hackernews, 2024).
According to Kaspersky Labs, although the initial understanding was that the backdoor allowed attackers to bypass Secure Shell Daemon application for sshd, for context, OpenSSH daemon is the server-side component of the OpenSSH suite, often referred to as SSH, is a cryptographic network protocol that allows secure remote login and other secure network services over an insecure network. While the initial assumption was understood as the backdoor that could bypass sshd, Kaspersky Labs has classified the vulnerability as “remote code execution” (RCE) (Kaspersky daily, 2024).
Latest update
Although the initial assumption held it as an SSLD bypass, the current update described the malicious backdoor intercepting the RSA public decrypt function. They check if the sender’s signature matches the fixed key Ed448 . If verified, the attackers can run any harmful code of their choosing, using a system () function and the whole process doesn’t leave any evidence in the logs of the secure shell server (sshd), thereby giving the impression that sshd logs have been bypassed.
Which packages are affected?
The following list of Linux distributions is affected by the backdoor, and the list is being updated as further analysis is conducted.
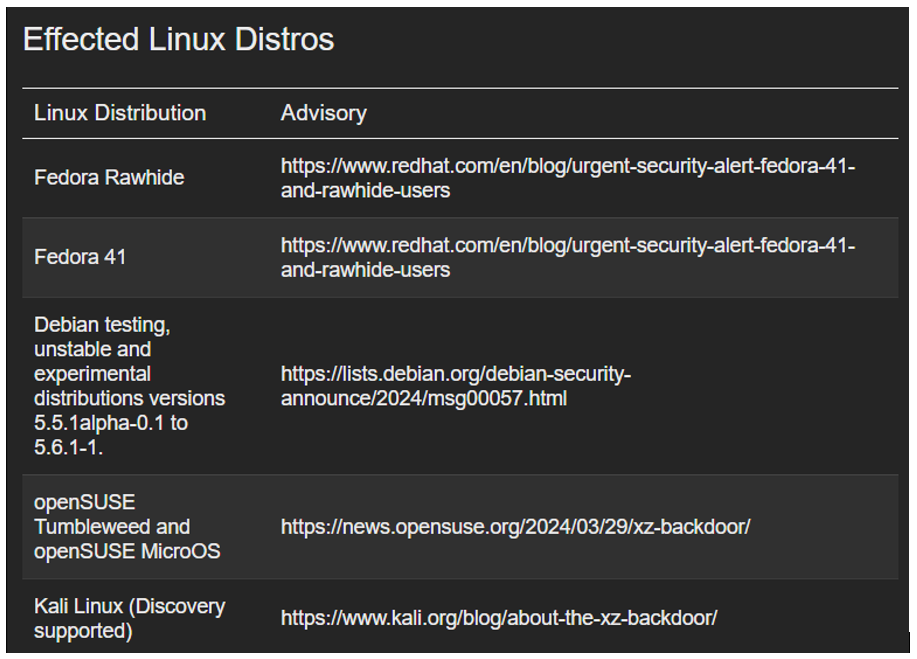
Figure 01 Source: (Brekkan, 2024)
Conclusion
To fully understand why this breach is significant, one must grasp the concept of an open-source or free software system. According to the GNU free software foundation, it can be defined as free software (GNU, n.d.)
“The users have the freedom to run, copy, distribute, study, change and improve the software.”
Although many would account for this vulnerability due to a lack of security checks for those who maintain the concerned libraries, it’s essential to recognise the immense effort and dedication of volunteers who tirelessly update and maintain these packages. Their work is fuelled by passion and personal growth, not simple monetary gain. The open-source community, a cornerstone of modern software development, is not immune to vulnerabilities; even the famous Kali Linux distro used by pen testers worldwide was affected by this vulnerability precisely because of its open-source packages. In light of CVE-2024-3094, the Kali official page advises users to update their systems if they haven’t done so after 29th March 2024 (Kali Org, 2024). The underlying issue lies in the open-source community’s challenges, particularly in how understaffed and underfunded such projects are already, and packages maintained by a single person are always prone to social engineering tactics. A Forbes article describes how “95% of vulnerabilities are found in transitive dependencies” (Badhwar, 2023). Even the XZ library was not infected in a day as the user Jia Tan, or JiaT75, was able to infect the system in a timeline of over three years with OSINT information about the user revealing the user IP to be a proxy in Singapore (Boehs, 2024). As the case stands, people who use such tactics rarely leave any digital dust. The solution requires a two-pronged approach in the face of state-sponsored threat groups, which constantly discover new ways to breach systems and exploit vulnerabilities. First, corporations must invest more in open-source projects they currently benefit from without contributing back. Second, companies using these packages must commit to regular vulnerability scans of their dependencies. This is crucial because the volunteers who maintain these packages often go uncompensated for their work, leaving the responsibility of ensuring system security to the user.
To conclude, the zero vulnerability scenarios are ever-increasing in the age of AI. While machines have become more competent, the human counterpart has become even more innovative in finding out the chinks in the Armor. Additionally, since most open-source packages depend on one-man teams, as in the XZ instance, the hope remains that the occasional discovery of zero-day vulnerabilities will continue to serve as a reminder of the ongoing need for vigilance and innovation in cybersecurity. The only difference this time is that instead of attempting to breach the system’s most robust defences, the threat actor targeted its most vulnerable link. In the aftermath of the XZ breach, we must undertake new initiatives to bolster support for open-source developers and enhance the regulation of open-source packages. These efforts should aim to ensure that the use of open-source packages is governed more effectively without compromising the vibrant and collaborative culture that it fosters.
Works Cited
Badhwar, V. (2023, 26th May). The Hidden Risk Lurking In The Software Supply Chain: Transitive Open-Source Dependencies. Forbes: Retrieved 09th April, 2024, from https://www.forbes.com/sites/forbestechcouncil/2023/05/26/the-hidden-risk-lurking-in-the-software-supply-chain-transitive-open-source-dependencies/?sh=269c8b8d512f
Boehs, E. (2024, March 29). Everything I Know About the XZ Backdoor. Retrieved 11th April, 2024, boehs.org from https://boehs.org/node/everything-i-know-about-the-xz-backdoor
Brekkan, B. (2024, April 01). Microsoft FAQ and guidance for XZ Utils backdoor. Retrieved 09th April, 2024, Mircosoft Techcoomunity from https://techcommunity.microsoft.com/t5/microsoft-defender-vulnerability/microsoft-faq-and-guidance-for-xz-utils-backdoor/ba-p/4101961
Freund, A. (2024, March 29). backdoor in upstream xz/liblzma leading to ssh server compromise. Openwall Retrieved 09th March, 2024, from https://www.openwall.com/lists/oss-security/2024/03/29/4
GNU. (n.d.). What is Free Software? GNU Retrieved 09th April, 2024, from https://www.gnu.org/philosophy/free-sw.html
Hackernews, T. (2024, March 30). Urgent: Secret Backdoor Found in XZ Utils Library, Impacts Major Linux Distros. The Hackernews Retrieved 09th April, 2024, from https://thehackernews.com/2024/03/urgent-secret-backdoor-found-in-xz.html
Kali Org. (2024, 29th March). All about the xz-utils backdoor. Kali Retrieved 09th April, 2024, from https://www.kali.org/blog/about-the-xz-backdoor/
Kaspersky daily. (2024, 31st March). Malicious code discovered in Linux distributions. Kaspersky Retrieved 09th March, 2024, from https://www.kaspersky.com/blog/cve-2024-3094-vulnerability-backdoor/50873/
NIST. (2024, 03 29). CVE-2024-3094 Detail. National Vulnerability Database Retrieved 09th April, 2024, from https://nvd.nist.gov/vuln/detail/CVE-2024-3094















