Cellular IoT Modules (CIMs) have become a prominent part of our daily lives. From personal products to complex systems, they help devices connect remotely to the internet. However, as the People’s Republic of China (PRC) aims to gain a global monopoly over the production of CIMs, experts have raised concerns over its unethical usage and potential threat to national security. In this context, the article aims to illuminate the nature of threat and recommends policy guidelines for New Delhi to mitigate the issue.
Background on CIMs and Global Market Share
CIMs are pocket-sized components housed in larger devices that allow them to connect to the internet via cellular networks. It comprises of parts like chipset, memory card, antenna port and a SIM card slot. This allows the device to be remotely controlled and transmit and receive massive amounts of data (Harris, 2024). CIMs are utilised in a range of devices, from personal usage, such as surveillance cameras and drones, to larger systems in industrial settings, such as production lines and power grids (Wedd, 2020).
With the arrival of the fifth-generation (5G) mobile network, the future of CIMs looks promising. 5G would allow CIMs-embedded products like self-driven cars and immersive VR/AR devices to operate at faster speeds seamlessly. The estimated global market size of CIMs is predicted to grow from USD 71.1 billion in 2021 to USD 521.2 billion in 2031 (Harris, 2024). By the end of 2022, an estimated 20 billion units of CIMs were under use, and these numbers are projected to reach 31 billion units by the end of 2025 (Parton, 2024). Some key industries that will fuel the demand are retail, health care, manufacturing, logistics, and agriculture (Harris, 2024).
According to the Q1 2023 figures, China and India have emerged as the major markets. The top three applications where CIMs are being utilised are Smart Meters (15.8 per cent), Point of Sale (14.8 per cent) and Router/CPE (5.2 per cent). Currently, more than half of the global market share of CIMs is dominated by Chinese manufacturers, as visualised in the table below (Sinha, 2023; Mandal and Agrawal, 2023).
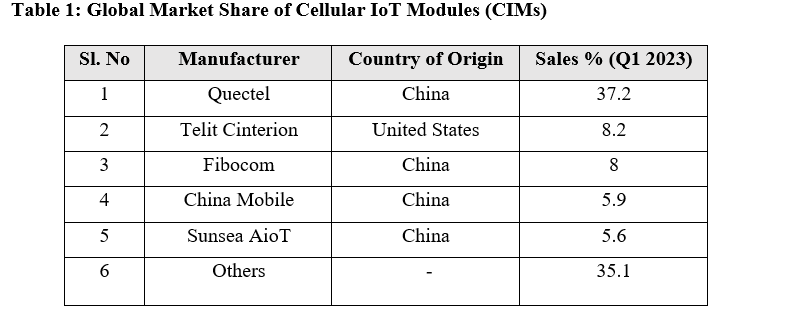
Data Source: https://www.counterpointresearch.com/insights/iot-module-shipments-q1-2023/
Nature of Threat
As Chinese manufacturers dominate the global supply of CIMs, experts have sounded alarm about the potential threat this could pose for other nations (Gokhale, 2024). The ability of the CIM to remotely receive firmware updates discretely without the end-user knowing opens up a window of opportunity for adversaries to manipulate the setting. The firmware updates could contain malware, allowing the Chinese suppliers to remotely control the device or shut it down and steal vast amounts of data to track user behaviour (Altavilla, 2023). In the US, the House Select Committee on the Chinese Communist Party (CCP) has raised concerns over the close links between the top CIM manufacturer Quectal and the Chinese military-industrial complex. It is reported that Beijing supports its domestic companies by providing subsidies worth hundreds of millions of dollars with the aim of controlling the market. The Committee has called for placing such untrustworthy suppliers on a prohibition list (Waterman and Tatlow, 2024).
International affairs expert Charles Parton views the nature of the threat to the national security arising out of Chinese monopoly over CIMs could emerge in three ways. First, Beijing can pressure dependent nations to modify their policies according to its interests or risk the supply of CIMs being cut off. Second, through malware designed as firmware updates, China can sabotage large-scale critical infrastructures like power grids and production lines. And third, CIMs can be utilised as gateways to hack into large amounts of unauthorised data. The data collected from devices can be effectively used to threaten key individuals and businesses (Parton, 2024).
Further, particular challenges may compound the nature of the threat arising out of the Chinese monopoly over CIMs. There is a lack of awareness among users regarding the nature of the threat, and there is a reluctance from the industry players to openly address the issue as they fear it may lead to short-term disruption in supply and profit (Parton, 2022). Since the CIMs are small and embedded inside large devices, its presence goes unnoticed. Even reputed Western companies like Tesla, Intel and Dell are known to use Chinese-manufactured CIMs (Drew, 2022).
Compliance Measures
In 2023, the global volume of IoT malware rose 37 per cent, totalling almost 78 million cases of cyber-attack (Business Standard, 2023). To address the security vulnerabilities, governments around the world have introduced compliance measures for the manufacturers. The “ETSI EN 303 645” is considered as the globally accepted standards for consumer IoT. The European Telecommunications Standards Institute (ETSI) is an independent organisation that produces globally applicable standards for information and communication technologies (ETSI, 2024). However, the development of universally accepted IoT regulation and compliance norms is still underway (IFACET, 2023).
The Department of Telecommunications under the Government of India launched the report “Code of Practice for Securing Consumer Internet of Things (IoT)” in Jan 2022 (PIB, 2022). The report borrows substantial inputs from the ETSI EN 303 645 and provides 13 baseline compliance measures. The important ones are no universal default passwords, to implement a means to manage reports of vulnerabilities, to keep the software updated and to securely store sensitive security parameters (TEC 2021).
Recommendations
India being the major source of demand in the global market for Chinese-manufactured CIMs. There is an urgent need to implement certain policies that will secure us from the impending crisis.
- The Indian Government must ensure standardisation, strict compliance, and testing of the CIMs supplied by foreign vendors against globally accepted security standards.
- India should develop its own indigenous IoT device cyber-security standards incorporating CIM security.
- Need to spread awareness among private and government users regarding the nature of the threat posed by Chinese-manufactured CIMs.
- To compile a list of untrustworthy Chinese suppliers and encourage procurement through trusted channels.
- Chinese-manufactured CIMs should be prohibited from being used in critical sectors like security, health, and power.
- Indigenous production of CIMs should be encouraged under the Atmanirbhar Bharat initiative.
- To collaborate with like-minded nations to address similar concerns and explore joint solutions to reduce dependency on Chinese-origin components.
Conclusion
Given its ubiquitous nature and the expanding cellular network, the use of CIMs is bound to grow. China aims to exploit this global demand by flooding the market with cheap alternatives to kill competition and ensure its monopoly. Hence, it is critical to address the issue by raising awareness about the nature of the threat posed by Chinese-manufactured CIMs and emphasising the procurement of such sensitive components via trusted channels. Negligence in failing to tackle the threat would lead to paying a high price in terms of a compromised national security.















