Of late, phishing has emerged as the most popular means of online frauds globally. The RSA Quarterly Fraud Report of 2018 establishes this statement citing how phishing accounted for 48 per cent of all cyber-attacks between January 2018 and March 2018, globally. What comes to us as a personal concern is that the same report also ranks India third in the list of the countries worst affected by phishing.[i] An almost coinciding picture emerges when data compiled at home is looked at. The National Crime Records Bureau, in its report of 2015-16, depicts a whopping 20 per cent rise in the number of cases reported for cyber-crime, of which 66 per cent involved online cheating.[ii] Adequate measures have been taken in the same direction, but the fact that over 80 per cent of these attacks in the country in 2017 had their origins in the remote jungles of Jamtara, a small district in Jharkhand, has kept the concerned authorities puzzled without relief for long.[iii] Provided that the district falls in one of the Maoist strongholds, the high possibilities regarding these funds filling Maoist coffers cannot be absolutely ruled out.
With acts of cyber-crime otherwise considered the plaque of the urban centres including Delhi, Mumbai, and even Kochi, the remote villages of Jamtara topping the phishing network of the country come as nothing less than a shocker to the concerned authorities and cyber-crime experts. These offenders use mobile phones as a means of phishing funds from bank accounts. A number of claims regarding the links of these cyber criminals and the Maoists infesting the area have come from the concerned police personnel. The recent data compiled by an Special Task Force of the UP Police shows that more than 2000 mobile numbers used for committing online fraud in the country have been traced back to this otherwise unknown place in Jharkhand. The additional Superintendent of Police with the STF, Dr Triveni Singh, believes that the smooth functioning of such activities in Jamtara is impossible without Maoist-support.[iv]
Jamtara: India’s Phishing hub
Jamtara came into existence in the year 2001 after breaking off from the Dumka district of Jharkhand, which is still among the 90 LWE-affected districts. Jamtara itself was listed as an affected district till as recently as 2015.[v] It is surrounded by the districts of Dumka, Deoghar, Giridh and Dhanbad, two of which are still, apart from Dumka, among the affected 90 districts. The fact that a significant number of these cases this year have been reported on outskirts of Jamtara, near the bordering districts, the geography in this context raises concerns.[vi] Moreover, it is an uneven terrain, with widespread forest stretches, low literacy and a majority of the population of approximately 8 lakhs attached to the primary sector, mainly rain-fed agriculture: all of which provide a fertile ground of Maoist operation. Most importantly, it is located at the junction of Jharkhand and West Bengal, which is a fairly lucrative location, considering the persistent loopholes in inter-state coordination of the State Police Forces. Cases of cyber-offenders crossing over State borders to evade raids and apprehensions have been consistently noted along this junction, like those at the active Chhattisgarh-Madhya Pradesh-Mahararashtra tri-junction, in the LWE-context, thus offering a suitable place of evasion, along with operation.[vii]
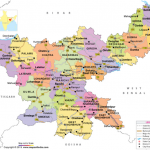
Jamatara is surrounded by Maoist-hit districts and lies at the junction of Jharkhand and West Bengal
It cannot be denied that the government clampdown on Maoist funding and activities, more successfully in Jharkhand than elsewhere, has triggered a sort-of existential desperation among the Maoists. Funding through alternative channels, therefore, is a choice they are likely to make, in an environment of already shrinking choices. Instances of the use of the intelligence networks of the Maoists by the cyber criminals of Jamtara to evade arrests and Police raids, on occasions more than one, only strengthen this possibility. The case of Ram Kumar Mandal, arrested in 2018, is a telling example in this context.[viii] The same incident also, therefore, makes one wonder as to why will the Maoists extend their intelligence to any other offender without any expected favours in return, considering their currently desperate position? Moreover, the use of cyber warfare as a means of expansion to urban centres forms an integral part of the document released by the Maoists as early as 2007. It states,
“We should, to the extent possible, make use of computers and the internet network to further the military objectives of the revolution. Though we are today quite distant from this possibility, we should have the perspective of setting up units with the task of damaging the military and other important networks of the enemy. The possibility of setting up such a structure however depends primarily on the development of the urban mass movement and the ability of the urban Party organisation to draw in and consolidate comrades with the required skills for such work.”[ix]
Concerns
The picture abroad only re-affirms the concerns laid down by the author so far. Instances of funds generated through phishing being routed to finance terror activities is an internationally recognised phenomenon. Terror outfits have, on several occasions, used online frauds to raise funds to match their financial requirements. The global anti-money laundering and terror financing watchdog, Financial Action Task Force, has noted the use of funds generated through credit card frauds by terrorist organisations like the al-Qaeda.[x] Similar instances of invoice redirect fraud have emerged from Ireland in Europe, which has been established as funding Islamic State activities in the war-torn West Asia.[xi]
With Jamtara offering a feasible location, both geographically, in terms of its proximity with Maoist strongholds, as well as with a state border easing evasion from police scrutiny when required; and socio-economic conditions including a part of over forty lakh landless agricultural workers of the state, ignoring the concerns seems rather problematic. Although the technological sophistication of these cyber criminals at present is of a basic standard, the probabilities of upgradation and modernisation, with the current pace of its growth with geometric progression, are not as unrealistic. In fact, the possibilities of the existence (or cocooning) of the ‘give-and-take’ relationship between the Maoists and the cyber offenders, exchanging the phished funds for timely intelligence and security, etc., are not absolutely improbable. Instances for the same already reported, although in fewer numbers as of now, stand testimony to this. Another point regarding whether these funds would be routed for “Party” benefit or individual gains by the Maoists in form of organised crime (as is more prevalent in Jharkhand) is also worth consideration while formulating long-term policies. (Currently, more than 12 splinter groups of the Extremists operate in the state, with the CPI (Maoist), People’s Liberation Front of India (PLFI), Tritiya Prastuti Committee (TPC), and Jharkhand Janmukti Parishad (JJMP) are the most active ones.) In the event of this synergy materialising in its full form and aggravating the security threats India currently faces, it becomes important for the Security Forces to prepare for the situation and take the required proactive measures.
References:
[i]“India among to 3 countries most targeted for Phishing: Report”, Economic Times, 25 May, 2018. Accesssed on 12 October, 2019. Available at: https://economictimes.indiatimes.com/tech/internet/india-among-top-3-countries-most-targeted-for-phishing-report/articleshow/64318150.cms?from=mdr
[ii]“India Today Investigation: Jamtara emerges as the biggest den of digital crime”, India Today, 3 January, 2017. Accessed on 11 October, 2019. Available at: https://www.indiatoday.in/india/story/india-today-investigation-jamtara-digital-hackers-cyber-crimes-953010-2017-01-03
[iii] Ibid.
[iv]“Online fraud major source of funds for Maoist rebels: UP Police”, Hindustan Times, 9 October, 2015. Accessed on 10 October, 2019. Available at: https://www.hindustantimes.com/india/online-fraud-major-source-of-funds-for-maoist-rebels-up-police/story-sMagmTgUlaubcKoEWLwPQM.html
[v]“Two more Santhal Pargana districts declared Maoist-hit”, The Times Of India, 21 December, 2015. Accessed on 13 October, 2019. Available at: https://timesofindia.indiatimes.com/city/ranchi/2-more-Santhal-Pargana-dists-declared-Maoist-hit/articleshow/50273702.cms
[vi] interview of Police Inspector from Jamtara Cyber Police Station with the author.
[vii]“An Empire built o stolen passwords”, The Times of India, 25 May, 2018. Accessed on 13 October, 2019. Available at: https://timesofindia.indiatimes.com/city/delhi/an-empire-built-on-stolen-passwords/articleshow/64311604.cms
[viii]Ibid.
[ix]“Urban Perspective: Our Work in Urban Areas”, Maoist Document, Available at: https://www.satp.org/document/paper-acts-and-oridinances/urban-perspective—our-work-in-urban-areas
[x]“How fraud is funding terrorism”, Rcounteur, 7 September, 2018. Accessed on 10 October, 2019. Available at:
[xi]“Bookies, banks and fraud: The methods Irish-based ISIS-sympathisers use to steal and funnel money cash”, thejournal.ie, 26 January, 2019. Accessed on 12 October, 2019.















