Abstract
Blockchain Technology as we know it today is no longer exclusive to cryptocurrency modules; any individual/party who knows cryptocurrency/bitcoin knows blockchain technology’s existence. Blockchain technology in its decentralized model was developed by an Individual or a group of people under the pseudonym Satoshi Nakamoto; the working theory and functionality of Bitcoin and Blockchain tech as we know it today was made public in the bitcoin whitepaper titled “Bitcoin: A Peer-to-Peer Electronic Cash System.” This minor paper will discuss Blockchain technology’s functionality and its apparent weakness against social engineering methods. (Nakamoto)
Introduction
Firstly, one must understand what makes blockchain technology unique, essentially an ever-growing interconnected digital registry. The Blockchain is a distributed ledger that is open and public. The open nature of the Blockchain makes it impossible to delete any data once it has been entered into the System. How does the blockchain work? Each block (data structure) in the chain consists of the data, the hash to that particular data and the previous hash makes it a continuous chain. The data recorded in the Blockchain depends on the type of Blockchain used; if it’s related to bitcoins, it will record information about transactions, the sender and receiver addresses, their transaction details, and the number of bitcoins present in all present blocks. Each new block is added to a chain by having its hash value that can be compared with existing hashes in other blocks; if two nearby hashes match precisely, then we know they come from the same block; otherwise, they’re not part of the same collection of transactions.
This System virtually ensures that any data fed into the blocks themselves are secure, further application of several measures such as “PoW, Proof of Work”, where each node is selected to create a new partnership in each round of consensus by computational algorithm, the participating nodes have to solve a cryptographic puzzle, the node which first addresses the block, as such even if one block would be compromised the computational power required to take control of the every corresponding node would be improbable since each additional node increases the difficulty of breaching the Blockchain.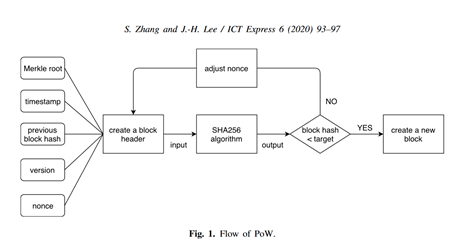
Figure 0.1 (Shijie Zhang, 2020)
The problem with security measures is that the thumb rule applies even to Blockchain technology; a chain is only as strong as its weakest link.
Social Engineering
Even though Blockchain is hailed as a robust model, it is not immune to social engineering because tactics employed in Social Engineering do not target the System itself but rather the human counterpart, which is more likely to make errors.
A definition of social engineering by Kaspersky Labs is as under:
“Social engineering is a manipulation technique that exploits human error to gain private information, access, or valuables. In cybercrime, these “human hacking” scams tend to lure unsuspecting users into exposing data, spreading malware infections, or giving access to restricted systems. Attacks can happen online, in-person, and via other interactions.”
As aptly put, Social engineering targets the individual rather than the System; in today’s social media platform, personal information is more public than it used to be, and even open-source penetration testing software like Kali Linux has widely accessible tools which make such tactics probable even by teens, packages like the Social-Engineer Toolkit (SET) hold inbuilt package which can conduct detailed attacks and even gather information on any intended target, for example, OSINT tools available in Kali Linux help one gather personal information of any intended target and if even a layman were to us packages like John The Ripper (Openwall, n.d.). It is in theory possible to crack many kinds of passwords, the package allows password decryption using dictionaries, brute force or a combination of the two paths; essentially, three modes can be used in this package single crack mode, wordlist mode, and incremental. The community version is free but lacks certain features. A paid version offers those extra features but requires a license to run. It’s possible to crack many kinds of passwords with john the ripper, including lower-case and upper-case variants; leet speaks slang terms, as well as some combinations thereof (for example: “sabre” + “mickey”). John will take a wordlist or dictionary file and try each password to crack the given file. In single-crack mode, john will take a wordlist file and try each password in it one by one until it finds the correct one for that particular file type (such as binary). In wordlist mode, john will take an encrypted file and try each word in its dictionary for passwords of that type before attempting encryption again with another hash algorithm or cracking method.
Now using social engineering tools, one can not only gather basic critical phrases of what an individual likes, such as their favourite animal, maiden name, and name of parents, but as such even more so they can infect an individual’s PC and steal passwords stored within the System itself. If blockchain technology were ever to be adopted in the Armed forces, it still bears the same weakness as Social Engineering tactics, even if a high-level official takes every precaution, just one member of their family failing to follow protocol can end up in a data breach, even with the advantage of the Blockchain system, if a black hat employs such tactics and gathers data of each corresponding node, the system would be down, in one swift swoop.
Conclusion
Since Blockchain is an upcoming technology and is being considered to be adopted in several fields and even armed forces as a whole, unless fully prepared to instil security protocols, the model may be more susceptible to be breached since Blockchain has received much hype in these past years, black hats will undoubtedly target the system, if security forces were to use it. The only way forward is to understand that social engineering is a legitimate threat to the blockchain system and learn how to reduce risk. While keeping in mind the probability of eliminating all risk associated is null.
Since the advent of IoT, information about developing and cracking is publicly available, and the present generation Z is more adept in learning tech; unless all precautions are in place, adopting blockchain technology may end in disaster.
The system is weak towards brute force attacks, in an instance where black hat tries all possible combinations of passwords until one is found that works on your target system. This is not good for anyone since it visibly takes up a long time and uses up resources, but it can be used in combination with social engineering attacks to quickly break into a company’s systems. The technology behind Blockchain requires the individual participants to share their private keys before they can complete the transaction. This makes the Blockchain vulnerable to brute force attacks where hackers try all possible combinations of private keys until they find one that works. The problem with Blockchain is that there are only so many combinations of private keys that a hacker can generate, but there are an almost infinite number of possible combinations for social engineering hacks. This means that hackers will always find a way into your system if you have not thought through your security measures properly — even if you have implemented multifactor authentication (MFA) or two-step verification (2SV), if a hacker has already accessed your systems via social engineering tactics it becomes visibly useless.
The only way forward is to step with great caution at every turn.
References
Fran Casino, T. K. (2019). A systematic literature review of blockchain-based applications: Current status, classification and open issues. Telematics and Informatics, 36, 55-81. doi:https://doi.org/10.1016/j.tele.2018.11.006.
Nakamoto, S. (n.d.). Bitcoin: A Peer-to-Peer Electronic Cash System. Retrieved November 16, 2022, from https://bitcoin.org: https://bitcoin.org/bitcoin.pdf
Openwall. (n.d.). John the Ripper password cracker. Retrieved November 21, 2022, from https://www.openwall.com: https://www.openwall.com/john/
Shiho Kim, G. C. (Ed.). (2020). Advanced Applications of BlockChain Technology. Springe Link. doi:https://doi.org/10.1007/978-981-13-8775-3
Shijie Zhang, J.-H. L. (2020). Analysis of the main consensus protocols of blockchain. ICT Express, 6(2), 93-97.















